In the IoT world, device identity and security are critical. One of the most common mechanisms mobile operators use to control access is the IMEI lock, which can determine whether connected devices are allowed on a network or blocked. There is also a user configuration of IMEI lock, where a user wants to make sure that a SIM will not be used in any other device than the one intended.
What Is IMEI?
Every mobile phone, tablet, or cellular-enabled device carries a unique fingerprint: the International Mobile Equipment Identity, better known as the IMEI. This 15-digit number is hardcoded into your device at the time of manufacturing. It cannot be easily changed, and changing it is illegal in most countries. For example, in the U.S. and Canada, changing an IMEI is considered tampering with a federally regulated identifier, while in the UK, it is illegal according to the Mobile Telephones (Re-programming) Act of 2002. Even in regions where changing an IMEI is not explicitly illegal, it can still lead to prosecution under fraud, theft or tampering laws as it can enable criminals to bypass blacklists, and undermine consumer protection and carrier security. Think of the IMEI as your device’s passport. Just as a passport allows authorities to identify you when traveling, the IMEI allows mobile networks to identify your device when it tries to connect. The IMEI does not change if you swap SIM cards, reset the phone, or even move across countries.
This number helps with several important functions, including:
- Device Tracking: Networks and regulators can locate or block lost devices.
- Fraud Prevention: Cloned or unauthorized devices can be quickly detected.
- Network Access Control: Only approved devices can connect.
In short, your SIM card tells the network who you are as a subscriber, and the IMEI tells the network what device you are using.
What Is an IMEI Lock?
An IMEI lock (also known as IMEI blocking) occurs when a mobile network or regulator prevents a device from accessing cellular services because of its IMEI number. Even if you insert a valid SIM card with an active data plan, the locked device will not connect to the network.
If a device has been blocked, you may see messages like, “Device blocked by network”, “IMEI is locked” or “no service”, even if the SIM is working as intended.
This can happen for a number of reasons. The device may have been reported lost or stolen, the account related to the device may have violated the contract, or the device may be restricted by local regulatory laws.
Even for an everyday user, this is frustrating. But for businesses managing large fleets of IoT devices, IMEI locks can create serious disruptions if they are not anticipated and managed properly.
How IMEI Locking Works
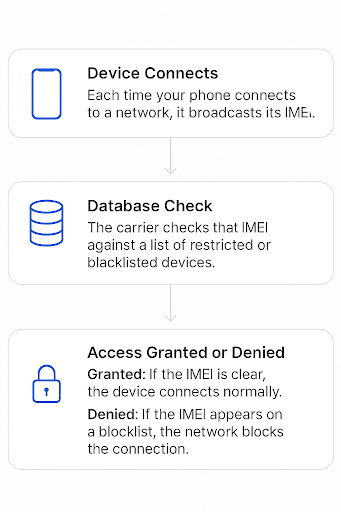
The process of IMEI locking takes place across three steps:
- Device Connects: Each time your phone connects to a network, it broadcasts its IMEI.
- Database Check: The carrier checks that IMEI against a list of restricted or blacklisted devices.
Access Granted or Denied: If the IMEI is clear, you’re connected. If the IMEI appears on a lock list, the network blocks the connection.
Most countries use one of two systems. They either have a centralized database, like in India, where the CEIR (Central Equipment Identity Register) allows all carriers to share blacklisted IMEIs, or they have operator databases, where each mobile operator has its own blacklist. Globally, the GSMA IMEI Database serves as a common reference point, enabling operators around the world to share information about stolen or blocked devices.
This means if your device is reported stolen in one country, it may be blocked in several others as well, depending on how widely carriers share data.
Why Is IMEI Network Locking Used?
IMEI locking exists for both security and business reasons. Here are three of the most common:
- Theft Deterrence: A stolen device is worth far less if it cannot be used. This discourages theft and makes second-hand markets safer.
- Fraud Control: Criminals sometimes use cloned or unauthorized devices. Blocking suspicious IMEIs helps stop fraud before it spreads.
- Regulatory Compliance: Some governments require networks to restrict unregistered devices for national security or consumer protection. For example in Turkey, you must register the device IMEI within 120 days of activation in the country.
For IoT and enterprise use cases, IMEI locking can also be used as a tool to control which devices are allowed to operate within a private or public mobile network.
Types of IMEI Locking
IMEI Blacklisting
IMEI blacklisting happens when a device is reported lost, stolen, or flagged for fraud. Its IMEI number is added to a shared blacklist (sometimes across multiple carriers or even countries).
- Who uses it? Carriers and regulators.
- What does it achieve? Prevents the specific device from connecting to most participating networks.
- IoT relevance: If an IoT device is stolen or compromised, blacklisting makes it useless on legitimate networks.
IMEI-Based Network Restrictions
Unlike blacklisting, which is usually about security and theft prevention, IMEI-based network restrictions are about control and policy enforcement. In this case, a carrier or enterprise deliberately restricts which devices can access their network, based on IMEI.
- Who uses it? Carriers, private networks, and enterprises.
- What does it achieve? Ensures that only devices with approved IMEIs are allowed to connect.
- IoT relevance: This is often used in enterprise IoT deployments where companies want to prevent unauthorized or counterfeit devices from joining their private networks.
Limitations of an IMEI Lock
IMEI locks are useful, but they are not bulletproof.
There can be regional gaps if networks do not share their blacklists internationally, which means devices may still connect in a different region. Additionally, criminals can perform IMEI cloning, which can block devices accidently. Remember too that an IMEI lock blocks the device itself, but the SIM can still function in another device.
For businesses that manage thousands or hundreds of thousands of connected devices, relying on IMEI locks alone is not enough. The facility should be used alongside a comprehensive management plane which allows more granular control.
floLIVE’s Approach to IMEI Locking in the IoT World
In addition to IMEI-based protection that is offered by the MNO, when it comes to IoT devices, floLIVE uses an additional layer of security and visibility to protect users from unauthorized use of SIM cards. . floLIVE’s global connectivity platform couples the IMEI to the IMSI, which prevents the SIM being used in any device not intended by the user.
Additionally, advanced connectivity management means that businesses can centrally manage which devices connect, where they connect, and how data flows, all from one dashboard. This level of control ensures reliability, reduces security risks, and prevents unpleasant surprises like discovering that a device’s IMEI is locked after deployment, or realizing that an unattended IoT device has been tampered with, and a SIM has been misused behind your back.
Understanding IMEI Locking and its Limitations
An IMEI lock is one of the most important tools mobile operators and regulators use to protect users and networks. By preventing stolen or fraudulent devices from connecting, IMEI locking makes mobile ecosystems safer and more reliable.
However, IMEI locks are not perfect. They can be bypassed in some cases, may not apply across borders, and can frustrate consumers who unknowingly purchase blocked devices. For businesses, relying solely on IMEI locks is not enough to ensure secure, scalable connectivity.
With an IMEI that is coupled with the IMSI, and centralized, cloud-native connectivity management, enterprises can go beyond IMEI locking to achieve full visibility and control over every device in their fleet. Whether you are deploying IoT devices across one country or around the world, floLIVE provides the security and scalability you need.
If your business depends on always-on, secure connectivity, it is time to move beyond the IMEI lock, and instead embrace a smarter, global-first approach.





